Repeat Occurrence notification templates
How to set up the best repeat occurrence notifications
What should a repeat occurrence notification look like?
A good standard layout for repeat occurrences should be simple to set up and easy to understand.
As a starting point, we advise a four-step notification that follows this flow;
- The employee is notified about their action
- The employee is notified about their action and assigned a task to complete off the back of that action
- The employee is notified about their action, and an escalation occurs
- A blanket step that occurs for all actions is included
This fairly simple flow ensures the employee is notified at every point and a clear escalation path is followed. This can apply to multiple events, so you can use the same template across several events.
Cooldown and reset periods
It's important to set a cooldown and a reset timeframe in your JIT notifications. These allow you to keep the occurrence cycles running and gives your employees a chance to improve themselves as time goes on.
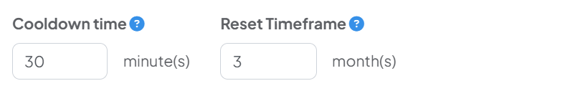
Cooldown time - If an employee triggers an event, then triggers another one within this time, it won't trigger the next occurrence. This gives employees a chance to read any notifications sent off the back of their actions.
Reset timeframe - The amount of time that will pass after an event has been triggered, before the occurrence sequence resets. If an employee triggers two events, after three months they will be reset back to the beginning. This allows employees to 'start fresh' and continue their learning cycle.
Notification templates
Everyone will have different cultures and tones they want to use for their notifications, you know your employees best, and what they will respond to better.
To help you get started and give some inspiration, we've created some basic templates in different tones that you can use and edit to suit your needs.
In these examples we'll be using the "Clicked a simulated phishing link" as an example. However, you can use these tone guides to create other notifications.
This template will make use of personalisation tokens, which will appear with '%%' at the start and end of the token, but when sent to the employee, they will format with the information inside the token.
These templates may not fit your exact structure or internal process and they take some assumptions of process for the sake of outlining examples, but you can use them as a starting point to create something that fits for you.
We'll give two example tone templates for you to use.
Light-touch, awareness focused tone
Using a friendly and informative tone of notification issues helps employees feel like you're here to help, not scold. This gentler, more casual approach can help employees feel less embarrassed when they make a mistake, and more likely to reach out for help when they need it.
-
Firmer, information-based tone
If you aim to emphasize the importance of employees being aware of their errors and recognizing the need to adjust their behaviour, adopting a more assertive tone can effectively convey this message.
By taking a firmer approach, you demonstrate a commitment to addressing insecure behaviours and highlighting areas for improvement across the board.
Clicking on a simulated phishing link
Engaging with employees who consistently click on simulated phishing links is important, consistent clickers highlights a gap in awareness that may escalate to opening real phishing emails.
Providing them with the necessary support and guidance to enhance their security understanding is essential to prevent potential security breaches.
In these templates, we'll inform the employee about their actions at every point, and escalate the problem as more clicks occur.
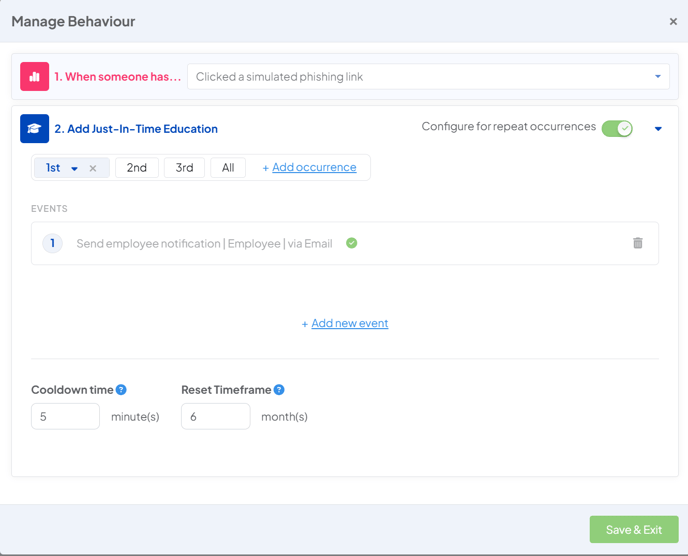
1st occurrence
The first time an employee clicks on a phishing link, you will send a notification to the employee to inform them about their click.
Clicking on a simulated phishing link for the first time isn't necessarily a bad thing, it can serve as a valuable learning experience. It provides an opportunity for the employee to understand the strategies used in phishing attacks, and how to better identify and avoid them in the future.
Light-touch, awareness focused tone
Hey there %%Common | Employee | Forename%%
You clicked on a phishing link, whoops!
Don't worry this was only a simulated phishing email! We all make mistakes and we want to help you improve your security savvy.
Here are some things you can look out for in the future to help you identify a fishy-looking phishing email;
- Spelling and bad grammar - Is everything up to snuff? Phishing emails will sometimes include poorly worded sentences or incorrectly spelt words.
- Call to action - Does the email seem oddly urgent, is it asking you to do something quickly with some sort of consequence if you don't?
- Links or unexpected attachments - Is there a link to click on, or a file to download? Check before you click on anything!
- Incorrect domains or links - Is the sender using the correct email? You can always search for a company's email to check if it's the right one.
Don't forget to head to your security centre to check your score!
Firmer, information-based tone
Hi %%Common | Employee | Forename%%
On %%Click Time%% you clicked on a phishing link.
This was a part of a simulated phishing campaign we're running to measure and improve our security awareness company-wide.
Please be more careful in the future.
Here are some things you can look out for in the future to help you identify Phishing Emails
- Spelling and bad grammar - Phishing emails will often use poor spelling and grammar.
- Call to action - Is it asking you to do something quickly with some sort of consequence if you don't?
- Links or unexpected attachments - Is there a link to click on, or a file to download? Check before you click on anything.
- Incorrect domains or links - Is the sender using the correct email? Always search for a company's email to check if it's the right one if you're unsure.
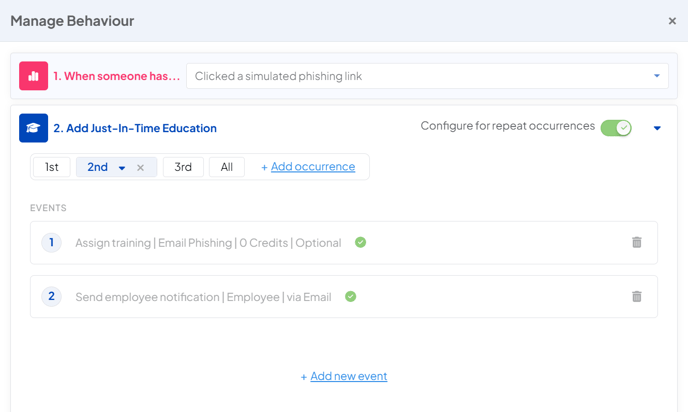
2nd occurrence
The second time an employee clicks on a simulated phishing link, you will inform them of this and direct them to complete some extra training.
Clicking on a phishing link a second time indicates that they have a lack of awareness for phishing emails. They haven't learnt from their previous mistake and are still susceptible to the same tactics and strategies used in phishing attacks.
Light-touch, awareness focused tone
Hey hey %%Common | Employee | Forename%%
We can see that you clicked on another phishing link at %%Click Time%%
Don't be upset, some emails can be hard to spot! We're running these simulations to give you the chance to train yourself and become a phish-proof fortress.
We assigned you a training module to help you avoid phishing emails in the future, you have 30 days to complete this, please complete this when you have the time!
If you feel like you need some extra help, please reach out to our cybersecurity team at helpcyber@company.com
They can give you some tips and pointers to help you better spot phishing emails.
Remember, look out for these in any emails you're sent;
- Poor spelling and bad grammar
- Call to action
- Links or unexpected attachments
- Incorrect domains or links
Firmer, information-based tone
Hi %%Common | Employee | Forename%%
On %%Click Time%% you clicked on a simulated phishing link, this had the subject of '%%Scenario | Subject%%' This is the 2nd time you've clicked on a phishing link.
This was part of a simulated phishing campaign we're running to measure and improve our security awareness company-wide.
We want to ensure you're getting the correct training you need to help you improve your security behaviours.
You have been assigned a training module in your Security Centre. This training module is mandatory and must be completed.
Please complete this as soon as possible.
-
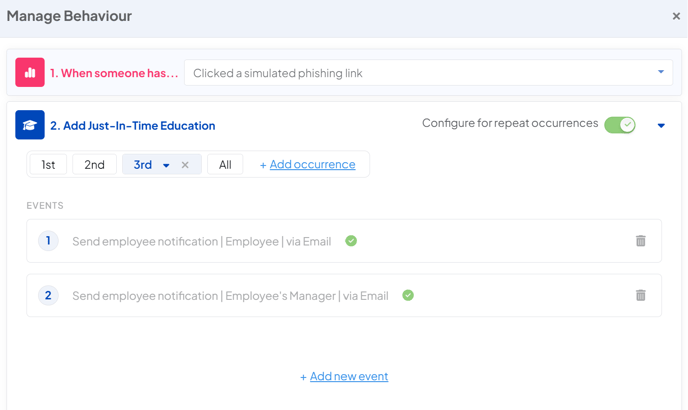
Third Occurrence
The third time an employee clicks on a simulated phishing link, you should be directly intervening and escalating the issue.
A third click indicates a serious awareness issue, that both JIT and conventional training methods have not improved. This speaks to the employees need for a different approach to learning about phishing.
For example, you could set up group training sessions for these employees, where they can speak to a member of the security team to ask questions, learn about phishing directly from someone involved in that area of your company and address their problems head on.
Light-touch, awareness focused tone
Hey %%Common | Employee | Forename%%
Oh dear, you clicked on a phishing link again!
We can see that you've clicked on a few simulated phishing links now. We really want to help you get your security skills up and help keep our company secure.
We've let your manager know (don't worry! You're not in trouble), so they can book you a meeting to go through some email phishing training, answer any questions you might have, and send you some resources you can use to check before you click on an email.
Firmer, information-based tone
Hi %%Common | Employee | Forename%%
On %%Click Time%% you clicked on a simulated phishing link, this had the subject of '%%Scenario | Subject%%'
This is the third time that you have clicked on a phishing link.
As a result of this, we will be passing this on to your line manager, they will assign to a training meeting that you must attended. They will contact you soon with further details.
If you have any concerns, please reach out to your manager.
-
Manager notification
Hi,
An employee you manage has clicked on a simulated phishing email three times.
As a result of this, they are required to attended a training session.
Please add %%Common | Employee | Forename%% %%Common | Employee | Surname%% %%Common | Employee | Email%% to the next available cyber security session.
All Occurrences
You should set an "All" step within your notification. This will apply to all occurrences of a click, no matter how many times the employee has clicked on a simulated phishing link.
You should set this to assign JIT-Training like the below;
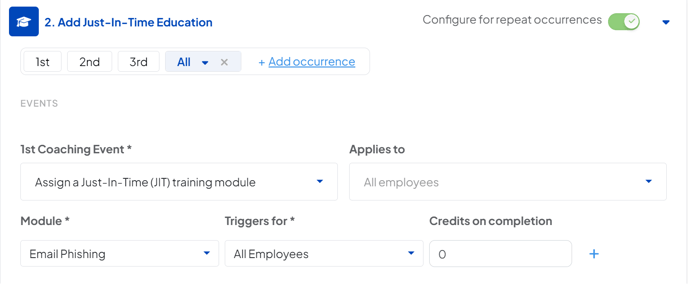
This will send a bite-sized instant module for employees to complete when they click on a phishing link.
For information about JIT-training, please click here.